Tutorials, instructions, technical terms
There are 3 types of network or group structures: centralized – decentralized – distributed

Centralized network

Decentralized network
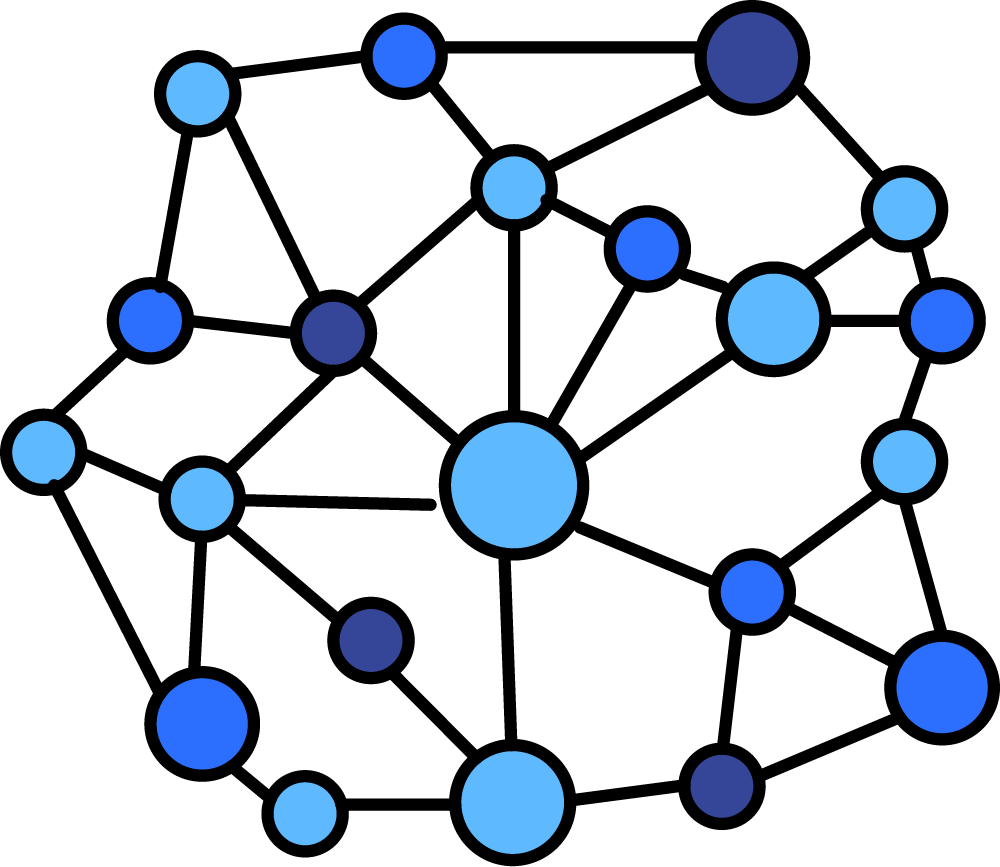
Distributed network
Each way of organizing has its advantages and vulnerabilities: centralized organization is the most effective in transmitting information, being direct, but it is precisely for this reason the most vulnerable to attacks, having only one point of failure. A compromised member can be quarantined or excluded, but if the central member is compromised, the entire organization / network will be instantly affected and automatically disconnected from the rest of the network.
Distributed organization is the most resistant to network attacks and corruption, any compromised point having no effect on the network / organization than other individual members. However, the speed of transmission and verification of information is the slowest, each member having to check all other members to ensure consensus.
Decentralized organization where each member connects to a network node, synchronizing them, combining both the resistances to attacks and the efficiency of network information transmission with synchronization between network nodes. The compromised nodes will be excluded from the rest of the network, affecting only the members connected to them. Affected members have the freedom to separate and reconnect to another node that has not been corrupted.
Byzantine General - consensus without central authority
Suppose you are a general who wants to conquer a castle. If you suddenly attack it with your allies and surround it, you can conquer it. Otherwise you will be overcome. How do you make sure all your allies:
– received the message to attack simultaneously
– You have all arrived to a consensus to act (attack)
– You removed all the spies sent find out about the attack
– You have excluded traitors or compromising generals that could break your plan
– You can not give orders to the other allies who have the same rank as you and do not recognize your authority over them (without any central authority)?
This is a mathematical problem proposed in 1975, considered unresolved until Blockchain technology proved to be its solution.
– real-time sync between “nodes” ensures that the entire network has the current information
– consensus is reached by miners checking transactions, competing against time between them, including checking previous transactions
– Private key cryptography ensures that only their owner can sign transactions and messages, transfer values to blockchain
– Network nodes and “miners” who do not “play” according to pre-established rules will automatically be excluded from the main blockchain, competition between them to reward “mining” motivating them to remain fair, being checked by the rest of the miners.
– on blockchain everyone has the same rights to move freely, to vote, to join or to separate from the rest of the network, the interest of everyone being to remain on the blockchain on which most of the participants are.)
What are the uses for Blockchain?
- Digital identity and citizenship
Practical applications: Individuals: Civic, Onename (onename.com); Companies, organizations: Aragon - Documents, diplomas, certificates
- Smart contracts: simple programs scheduled to run automatically on the blockchain
- Practical applications: Ethereum, Waves, Neo, Lisk, Rootstock
- Security: through the decentralized structure and a mechanism driven by consensus
- Private governance and digital voting
- Reputation based pseudo-anonymity
Aplicație practică:
- Unique physical properties recorded on the blockchain:
Practical applications: art (Verisart), honey and hives (Apis) - Decentralized Online Shop: Practical applications: Openbazaar
- Decentralized notary
- Recording and track real-time physical goods shipments
Practical applications: Tracking phisical goods and rransfers (BitNautic) - Utilization of unused computer resources
Practical applications: Encrypted hosting and redundancy on blockchain (Sia, Filecoin, Stroj), Processing Power and Artificial Intelligence (Golem, Augur)

